Is Security in Direct-to-Cell Networks Really as Fragile as Critics Say?
Jun 16, 2025
For decades, mobile connectivity has been fundamentally tied to land-based infrastructure, requiring extensive networks of cell towers, fiber optic cables, and base stations to provide communications services. The traditional model has been valuable to billions of users but has its limitations in reaching remote locations, disaster areas, and maritime regions where infrastructure deployment is still economically unviable. Direct-to-cell (D2C) satellite communication is an emerging paradigm in this context, where regular smartphones can talk to low earth orbit satellites without special hardware changes or the need to carry extra equipment.
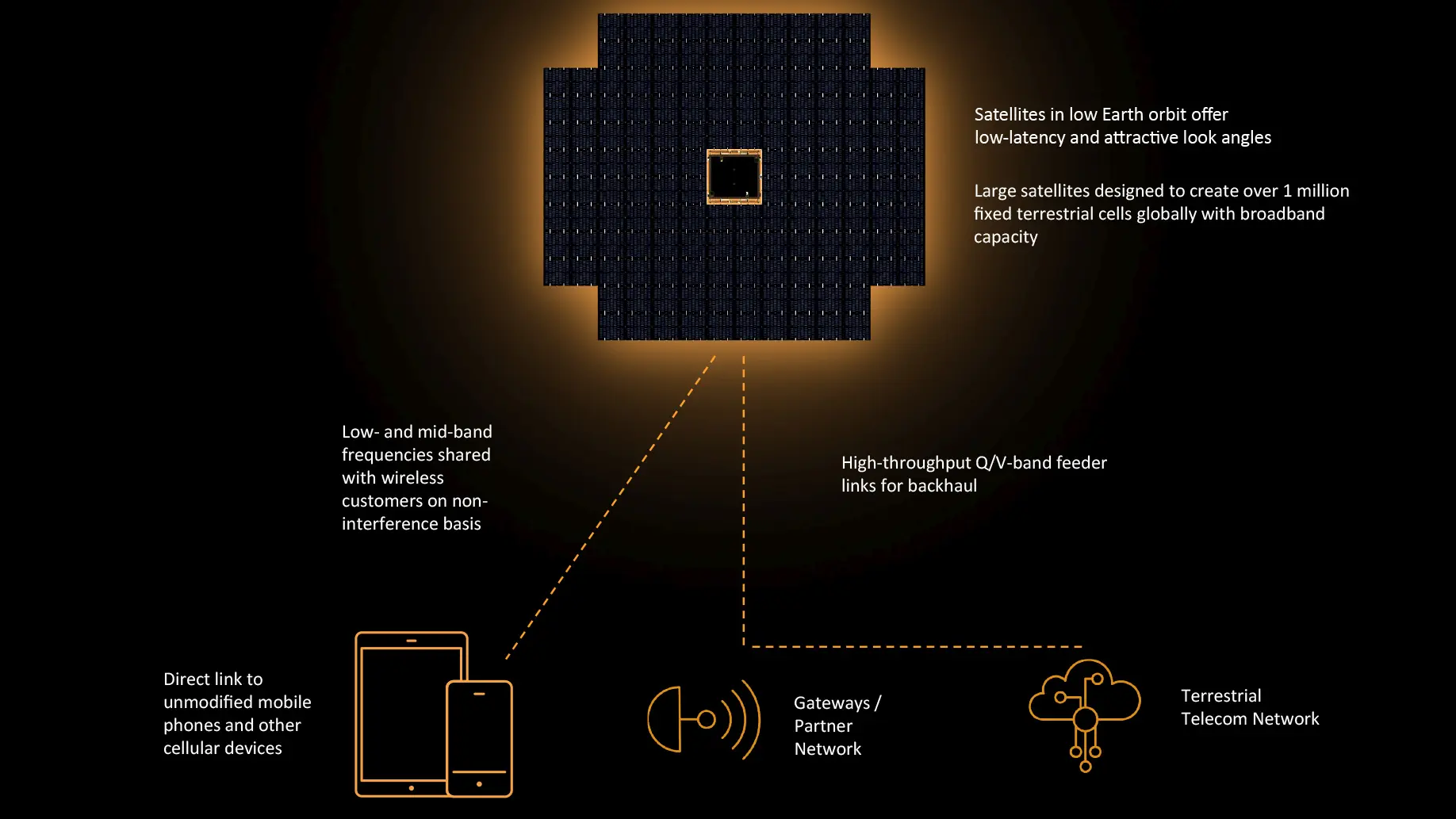 Direct-to-cell technology promo. Credit: AST SpaceMobile
Direct-to-cell technology promo. Credit: AST SpaceMobile
The transition between theory and practice has been quite rapid, and firms such as AST SpaceMobile and Lynk Global are taking a leading role, as are the largest mobile operators that see the strategic importance of satellite-terrestrial convergence. This technology holds the promise of eliminating coverage gaps that have plagued mobile networks in the past, providing truly universal connectivity, both in cities and far away in the most inaccessible regions of the world. The combination of the miniaturization of satellites, enhanced launch capacities, and advanced software-defined radio technologies has not only rendered D2C technically possible, but also commercially viable, which is a milestone in the development of telecommunications.
Addressing Exaggerated Security Concerns
With the rise of D2C technology, it is only natural that cybersecurity specialists have become particularly interested in this technology, with some of them describing it as a possible security disaster in the making. Although these concerns contain some rational elements, they tend to be part of a pattern of technological pessimism that has surrounded other major communications innovations in the past. Critics often refer to D2C as resulting in an unprecedented attack surface in space and claim that the technology is being launched with little to no thought on security protocols or regulation.
 KA-SAT satellite. Credit: Google
KA-SAT satellite. Credit: Google
But this description does not reflect the significant maturity that has grown both in the space industry and cybersecurity community since previous technological transitions. The development of D2C today is not taking place in the relatively immature security environment that was present at the time of 3G network deployments or even early internet infrastructure, but in a mature environment of well-established security frameworks, regulatory demands, and industry best practices. The adoption of encrypted telemetry systems, artificial intelligence-based anomaly detection capabilities, and defense-in-depth strategies shows that industry leaders are not waiting to see what discovered threats will do; instead, they are actively working to mitigate known vulnerabilities. Moreover, security architectures and operational procedures have been informed by lessons learned during past satellite incidents such as the well-known KA-SAT disruption and multiple interference incidents.
Acknowledging and Managing Inherent Risks
To realistically evaluate D2C technology, it is important to note that valid security concerns need to be addressed, including signal jamming and spoofing, as well as vulnerabilities in ground station infrastructure and satellite control systems. The space environment poses certain threat vectors unlike terrestrial communications, such as possible interference by state and non-state actors who might have advanced electronic warfare capabilities. Well-publicized cases like the KA-SAT modem interruption during recent geopolitical hostilities are a clear wake-up call to the understanding that satellite communications infrastructure can be an object of attack in the context of larger conflicts.
However, such threats should be positioned in the larger context of telecommunications security where similar threats have effectively been mitigated by technological countermeasures and operating procedures. The key distinction between modern D2C implementations is the degree of openness and urgency with which the sector is approaching these issues. Telemetry and control systems, which are universally acknowledged to be the most sensitive aspect of satellite systems, are becoming more secure with many layers of protection such as secure communication channels, multi-factor authentication mechanisms, and high levels of access controls that surpass those normally used to secure terrestrial infrastructure. Pre-deployment security assessments, red-team training exercises simulating advanced attack scenarios, and full hardening of physical and software assets have become commonplace practices in the industry. Although such measures do not completely remove all risks, they represent a huge step forward in proactive security planning compared to previous generations of satellite systems.
International Regulatory Framework and Cooperation
The idea that satellites are launched and used in a regulation-free zone, without proper oversight and security practices, is one of the most prevalent myths about D2C technology. This understanding is a complete distortion of the existing regulatory landscape, which entails massive cooperation between international organizations, national space agencies, and commercial operators. The United Nations Office for Outer Space Affairs (UNOOSA) has been involved in the central facilitation of discussions of space security norms, and national regulators like the Federal Communications Commission have stringent licensing provisions requiring thorough security evaluation prior to deployment of any satellite.
 The United Nations Office for Outer Space Affairs promo. Credit: UNOOSA
The United Nations Office for Outer Space Affairs promo. Credit: UNOOSA
D2C technology is developed in a more collaborative environment where more focus is given to public-private partnerships and information sharing. Security organizations and industry associations have developed common intelligence platforms that help quickly share threat information and best practices across the industry. Security systems based on existing standards like ISO/IEC 27001 are being customized to space-specific requirements, and coordinated emergency response procedures are in place so that incidents can be dealt with through collective effort rather than independent company responses. This model of collaboration is based on the successful standardization efforts of the aviation industry, which indicates that space communications may also reach the same level of safety and security through coordinated international efforts. The fact that defense organizations and national security agencies are part of the group working on the creation of cybersecurity norms shows that D2C development is getting the serious attention and direction of organizations with extensive experience in threat identification and mitigation.
Future Outlook and Resilience Building
D2C technology development has shown a mature realization that cybersecurity is not an end but a continuous process of adaptation and refinement. Industry leaders understand that threat actors will keep evolving their capabilities, and defensive measures should be built with enough flexibility to respond to new challenges. This philosophy is also expressed in the use of defense-in-depth security models that presuppose the need to have several levels of protection, the use of modern cryptographic algorithms that take into consideration future computing capabilities, and the implementation of thorough training programs for the workforce to detect and counter advanced attacks.
Incorporation of artificial intelligence and machine learning technologies into satellite operations is one of the most promising trends in improving security capabilities. Such systems can quickly process large amounts of telemetry data in real time, detecting anomalous patterns that could point to attempted intrusions or system malfunctions before they cause serious disruption. When matured, these technologies will likely offer capabilities beyond what human operators might achieve through manual monitoring. Regulators are also learning lessons from the past and adjusting their regulations to new technologies to ensure proper protection. Insurance firms are beginning to incentivize organizations that establish strong cybersecurity practices, providing market incentives to continue investing in defensive capabilities.